The air inside a modern data center hums with a controlled and constant energy. It’s a symphony of cooling fans, spinning disks, and the quiet, ceaseless flow of data through fiber-optic veins. In this meticulously managed environment, every component is engineered for reliability, from the powerful servers to the complex network switches. Yet, bolted to the back of the very racks that house this critical infrastructure lies a device that is often overlooked, a piece of hardware that has quietly evolved from a simple commodity into one of the most dangerous potential entry points for cyber adversaries: the Power Distribution Unit (PDU).
For decades, these were little more than glorified power strips. Today, they are intelligent, networked computers in their own right, offering granular control over the lifeblood of the data center—electricity. But this evolution has come at a cost. Recent research has pulled back the curtain on this innocuous hardware, revealing a landscape of critical vulnerabilities that could allow an attacker to shut down services, destroy equipment, and gain a crucial foothold deep inside the network perimeter. The question is no longer if these devices can be hacked, but whether the industry is prepared for the consequences.
The Quiet Evolution: From Dumb Strip to Smart Target
The journey from a basic power strip to an intelligent PDU (iPDU) mirrors the broader story of the Internet of Things: convenience and connectivity have created unforeseen risks. To understand the threat, one must first understand the evolution.
- The Age of Innocence (Basic & Metered PDUs): Initially, PDUs were simple distributors of power. Their only risk was physical. The first layer of intelligence came with Metered PDUs, which provided a local digital display of power consumption. Some offered a network connection for remote viewing, but the risk was minimal—an attacker might see your power bill, but couldn’t turn anything off.
- The Dawn of Control (Switched PDUs): The game changed with Switched PDUs. These devices gave administrators the power to remotely turn individual outlets on or off. This was a massive leap in efficiency, allowing for remote reboots of frozen servers. But it also meant that for the first time, a cyberattack could directly cut power to critical systems.
- The Hyper-Connected Endpoint (Intelligent PDUs): Today’s Intelligent PDUs (iPDUs) are the pinnacle of this evolution. They are fully-fledged embedded systems with their own operating systems, web servers, and command-line interfaces. They offer outlet-level monitoring, environmental sensing, and deep integration with Data Center Infrastructure Management (DCIM) software. This complexity, while operationally invaluable, has transformed the PDU into a rich and fertile attack surface, susceptible to the same kinds of vulnerabilities found in any other networked computer.

The Watchmen on the Walls: Researchers Sound the Alarm
The theoretical risk of PDU hacking became alarmingly real when cybersecurity researchers began to scrutinize these devices. At major security conferences like DEF CON, firms like Trellix and Claroty have presented damning findings, revealing a pattern of severe vulnerabilities across multiple major PDU vendors.
These weren’t minor bugs. The research uncovered critical flaws that could be exploited remotely, without authentication, to gain complete control of a device. Consider one of the most severe examples, CVE-2023-3259, a critical (CVSS 9.8) authentication bypass vulnerability discovered by Trellix in a popular PDU model. Researchers found that by manipulating a simple cookie in their web browser, an attacker could trick the PDU into treating them as a full administrator.
With that single, simple trick, an unauthenticated attacker from anywhere on the network could:
- Remotely shut down power to any server connected to the PDU.
- Change administrative passwords, locking out legitimate users.
- Create new user accounts for persistent access.
- Modify the PDU’s network settings to hide their tracks or launch further attacks.
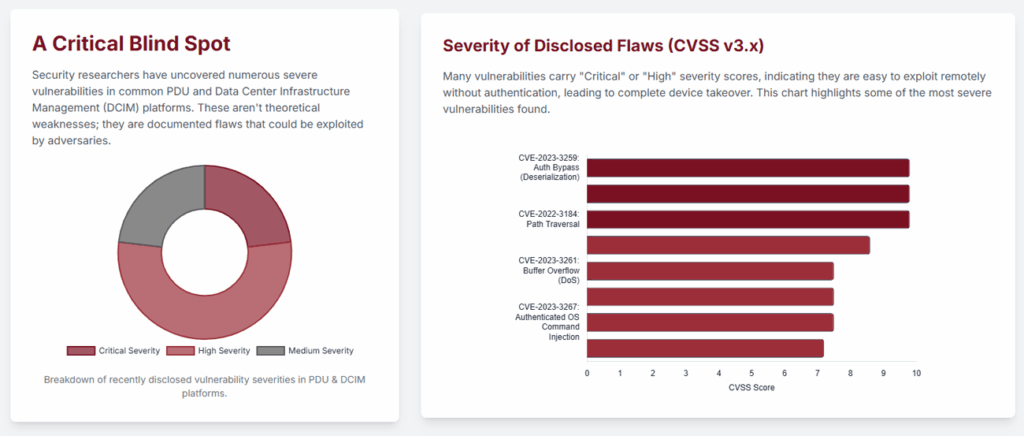
This is just one example among many. Other documented vulnerabilities have included OS command injections that allow attackers to run their own malicious code, path traversal flaws that give access to the entire file system, and the persistent use of hard-coded credentials that act as a universal skeleton key.
The Digital Domino Effect: When the Lights Go Out (And Worse)
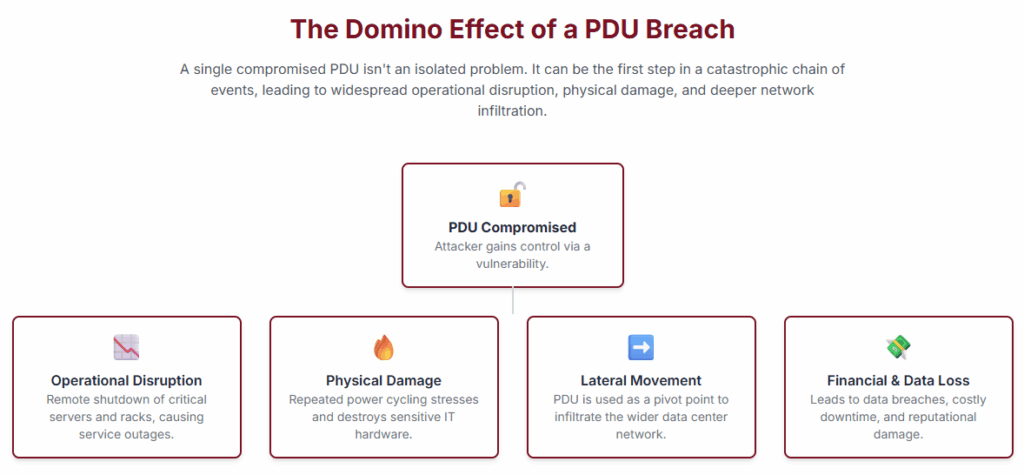
A hacked PDU is not an isolated problem; it is the first domino in a potentially catastrophic chain reaction. The consequences of a successful compromise are multi-layered and severe:
- Operational Disruption: The most immediate impact is a shutdown. An attacker could remotely turn off power to individual servers or entire racks, triggering immediate service outages, data corruption, and significant financial loss. In a world where downtime is measured in thousands of dollars per minute, a widespread power-down event is a nightmare scenario.
- Physical Destruction: More sinister than a simple outage is the potential for physical destruction. A compromised PDU could be used to repeatedly and rapidly power-cycle equipment, a process that puts immense stress on sensitive electronic components like power supplies and motherboards. This malicious cycling could lead to premature hardware failure and permanent damage, turning a cyberattack into a destructive physical event reminiscent of the Stuxnet malware that destroyed industrial centrifuges.
- A Beachhead for Deeper Infiltration: Perhaps the most dangerous long-term risk is that a compromised PDU provides a perfect “beachhead” for an attacker inside the network perimeter. Security teams often focus their monitoring on servers and workstations, but a lowly power strip is rarely given the same level of scrutiny. Once an attacker controls a PDU, they have a trusted, yet unmonitored, node on the network. From this foothold, they can launch further attacks, scan for other vulnerable systems, install persistent backdoors, and move laterally to steal data from the data center’s most valuable targets. The PDU becomes the ghost in the machine, a silent pivot point for a much larger breach.
Building a Digital Fortress: A Practical Guide to PDU Defense
While the threat is daunting, it is not insurmountable. Securing this critical infrastructure is paramount and requires a proactive, multi-layered approach that treats PDUs with the seriousness of any other critical network endpoint.
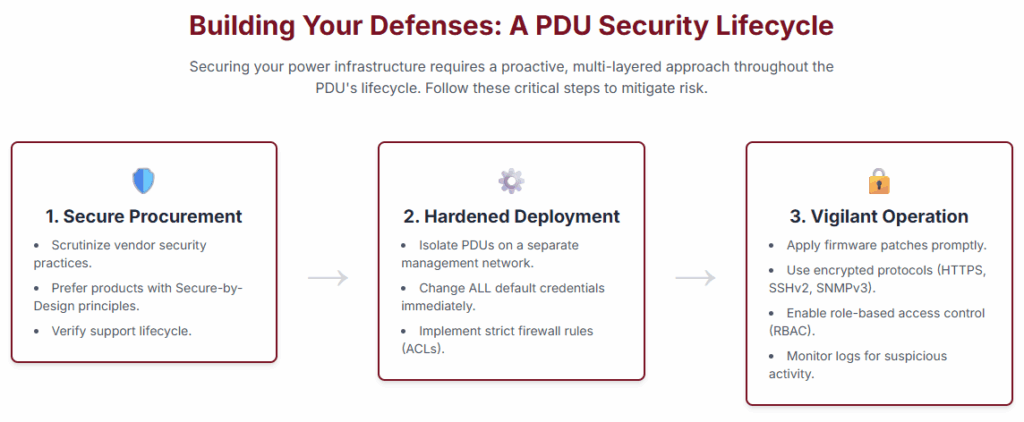
Principle 1: Isolate and Contain PDUs should never reside on the same network as general corporate or production traffic. They must be segmented onto a dedicated, isolated management network. Strict firewall rules and Access Control Lists (ACLs) should be implemented to ensure that only authorized IT staff from specific workstations can communicate with the PDUs.
Principle 2: Authenticate and Authorize Default credentials are an open invitation to an attacker. All default usernames and passwords must be changed immediately upon deployment. Enforce strong, unique passwords and utilize centralized authentication services like RADIUS or LDAP where possible. This ensures consistent policy enforcement and makes it easier to revoke access when an employee leaves.
Principle 3: Encrypt and Harden All management traffic to the PDU must be encrypted. Disable insecure legacy protocols like Telnet and unencrypted HTTP, and use only secure, modern alternatives like SSH and HTTPS. Furthermore, disable any services or ports on the PDU that are not absolutely necessary for its function to minimize the available attack surface.
Principle 4: Patch and Protect You cannot protect what you do not know you have. Maintain a precise, up-to-date inventory of all PDUs, including their model numbers, firmware versions, and network locations. Monitor vendor security advisories and apply firmware updates and patches as soon as they are tested and validated. An unpatched PDU is a ticking time bomb.
The power strips in your data center are no longer simple hardware. They are complex endpoints that demand the same level of security scrutiny as your most critical servers. The findings from the security community are a clear call to action. Ignoring the threat in the rack is not an option—it’s an invitation for an outage, or worse. It’s time to ensure that the devices that power your infrastructure are not the very things that bring it down.
Learn More

| White Paper – Data Center Power Distribution Units – Vulnerabilities, Impacts, and Mitigation Strategies delves into the critical security considerations surrounding these essential components. Discover: > The Evolving Threat Landscape > Documented Vulnerabilities > Potential Impacts of a Breach > Actionable Mitigation Strategies |
Securing Data Centers: The Imperative of Keeping Firmware Up to Date – AutomatedBuildings.com




One Response